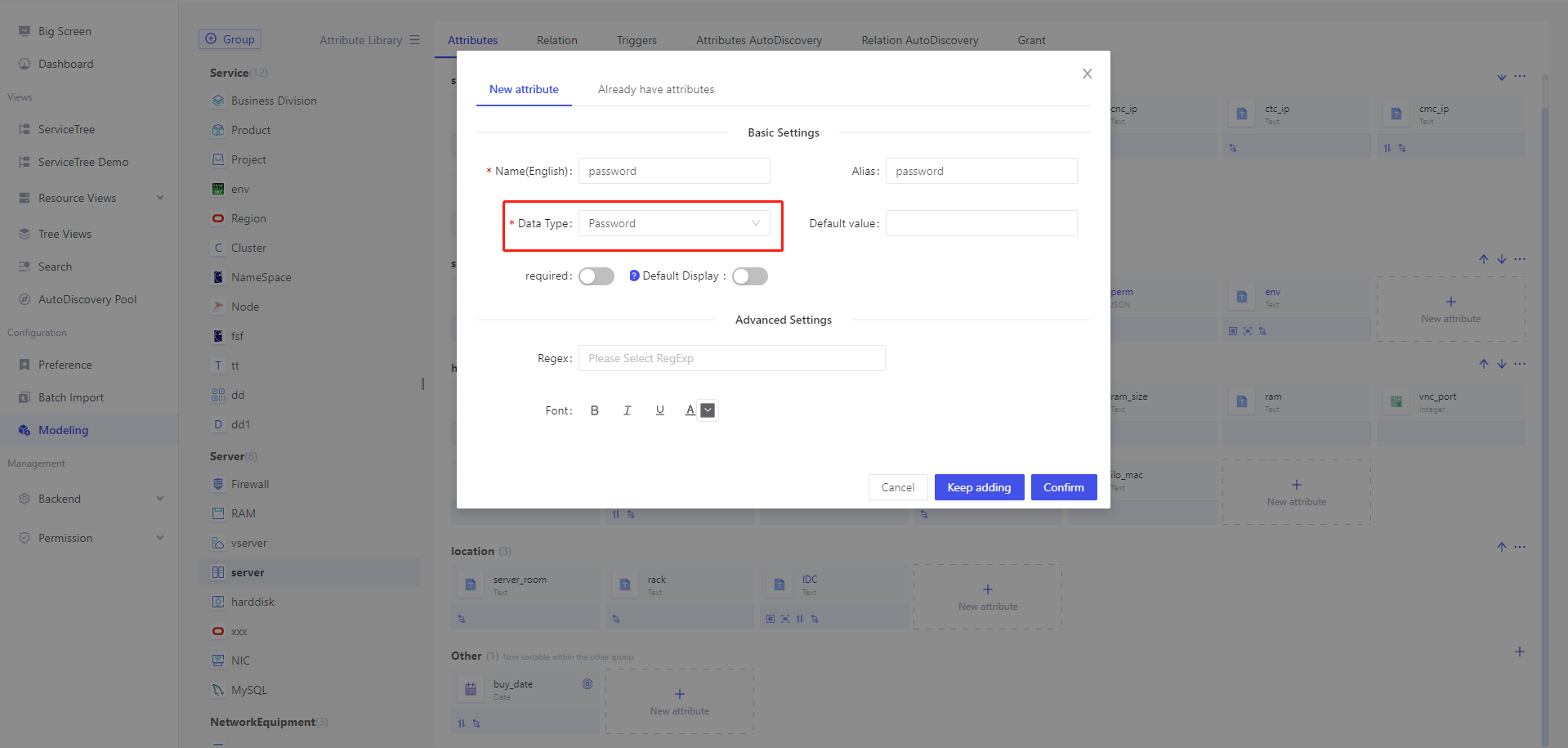
Password Storage
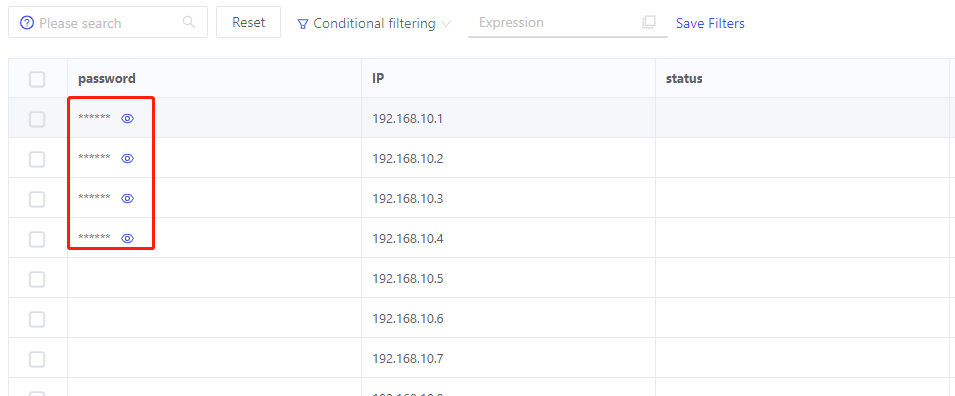
The data types in Veops CMDB support passwords. The password attribute ensures that sensitive user information (such as passwords) is protected during storage and transmission, preventing unauthorized visitors from obtaining and tampering with user password information. Encryption processing improves system security, reduces the risk of password leakage, and protects users' private data from being stolen by malicious attackers. This helps to ensure the confidentiality and integrity of the system and user data, and enhances the security and trustworthiness of the system.
The platform supports two forms of storage, one with built-in storage encryption (INNER), and the other with support for interfacing with other password management systems, which currently supports VAULT.
internal storage
The current configuration defaults to the built-in storage method, i.e. SECRETS_ENGINE="inner" in the configuration. When preparing to use the built-in method, you need to manually initialize the built-in storage system first.
1. initialization
Before the service can be started, various keys need to be generated using the initialization command.
flask cmdb-inner-secrets-init
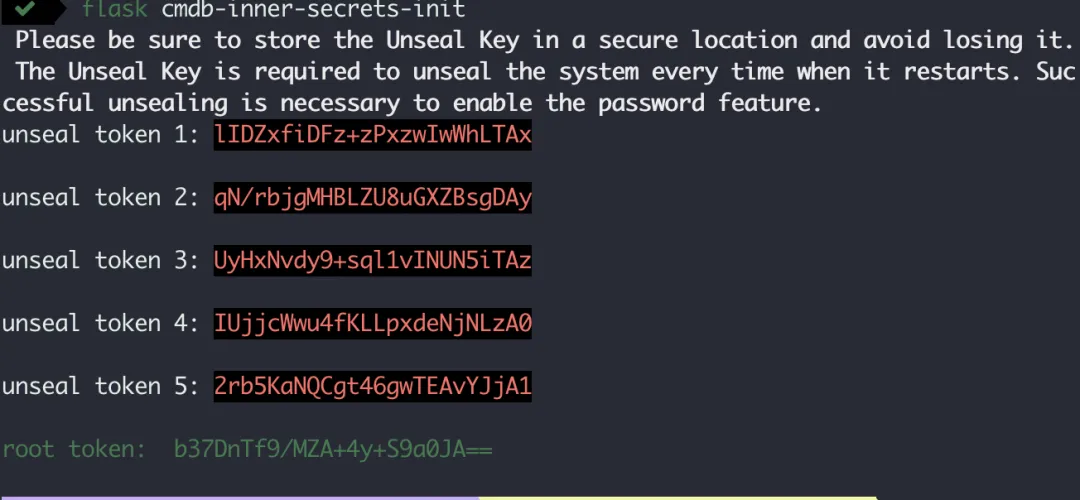
After successful initialization, the terminal will output five unseal keys and one root token. You need to save these keys manually and put them in a safe place for later safe use, otherwise it will lead to the subsequent inability to unseal the secret key, which will make the cryptographic function unavailable.
The easiest way to do this is to put a root token in the INNER_TRIGGER_TOKEN field in the api container's settings.py configuration file and restart the api service.
2. Unblocking (optional)
Unblocking is to activate the password service function of the system. By default, the service needs to perform the operation of unblocking every time it is restarted, and the unblocking operation is performed using any three unblocking secret keys generated during initialization.
flask cmdb-inner-secrets-unseal -a http://127.0.0.1:5000
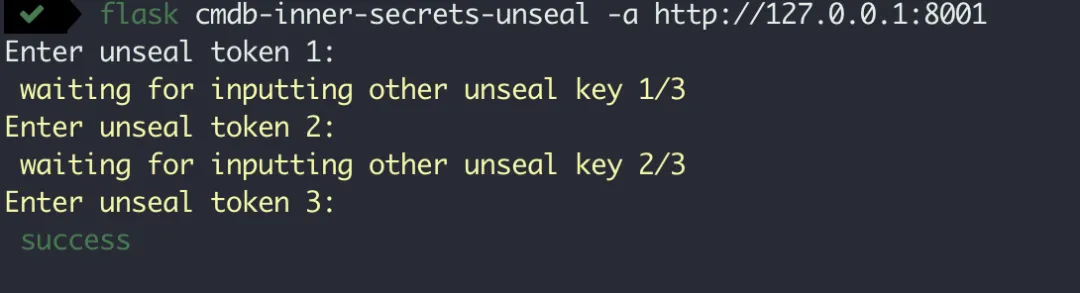
If it is more troublesome to unseal the token every time you start, the system also supports automatic unsealing, that is, in the configuration, the root token will be placed in the configuration file, so that you can realize the function of automatic unsealing, but this will sacrifice part of the security. Of course, you can also configure its value as an api address, and the system will automatically call the api to realize automatic unblocking.
INNER_TRIGGER_TOKEN = ""
3. Sealings (optional)
This feature is optional, i.e., you can choose to temporarily disable the password service, after which you will not be able to perform the read and write functions of passwords, or you can seal it via the API.
flask cmdb-inner-secrets-seal -a http://127.0.0.1:5000
vault
vault is a widely recognized open source password management system, and if you are using or wish to use it as a backend for password storage, it is also supported in the current release.
The transit encryption engine of vault and the back-end kv cipher engine are used. To use it, you just need to create a kv cipher engine with the name CMDB in vault and specify the following information in the configuration file.
SECRETS_ENGINE = 'vault'
VAULT_URL = ''
VAULT_TOKEN = ''